Key Payment Crime Trends from the FBI's 2024 Internet Crime Report
Published on May 9, 2025
AUTHOR
Eric Wester, AAP, AFPP, APRP, NCP
Associate Director of Education Services
The FBI’s recently released 2024 Internet Crime Report (off-site) underscores a significant escalation in cyber threats. With reported losses exceeding $16 billion—a 33% increase from the previous year—the data highlights the continued need for financial institutions and their clients to be proactive in protecting themselves.
This surge in cybercrime highlights the evolving tactics of cybercriminals and the increasing sophistication of their schemes. For stakeholders in the payments industry, understanding these trends is crucial for developing effective countermeasures and safeguarding financial transactions.
In this blog, we explore the key findings of the 2024 Internet Crime Report, focusing on Business Email Compromise and offering insights into how businesses can enhance their cybersecurity posture in response to these emerging challenges.
Business Email Compromise
At UMACHA, one of the most common payment-related fraud schemes we hear about is Business Email Compromise (BEC), and it’s a crime trend we closely monitor.
BEC is a type of cybercrime where fraudsters use social engineering and email spoofing or hacking to trick employees—often in finance or executive roles—into transferring funds or sensitive information to the attacker. These emails appear to come from trusted sources, such as company executives, vendors, or partners, and often involve urgent or confidential requests.
In 2024, there were 21,442 BEC complaints, with losses totaling $2,770,151,146, representing a small decrease from 2023.
| Business Email Compromise Complaints and Losses by Year | |||
|---|---|---|---|
| Year: | 2024 | 2023 | 2022 |
| Number of Complaints: | 21,442 | 21,489 | 21,832 |
| Complaint $ Loss: | $2,770,151,146 | $2,946,830,270 | $2,742,354,049 |
BEC is not limited to any one particular payment type, and fraudsters have shown they will perpetrate this type of scheme to induce payments under false pretenses that result in ACH credits, wire transfers, instant payments, or any other method by which the sender can remit funds and push a credit to either the fraudster or someone under the fraudster’s control (such as a money mule).
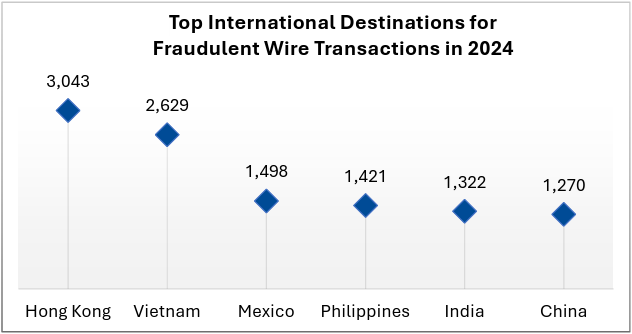
(Illustration representing the top international destinations for fraudulent wire transactions from calendar year 2024.)
There are several techniques financial institutions and businesses alike can employ to help protect themselves from BEC schemes:
-
Verify Payment Requests Through a Secondary Channel: Establish procedures to confirm requests for fund transfers or changes in payment information via a known phone number or in-person contact, not just email.
-
Train Employees to Recognize Red Flags: Provide regular training to employees on how to spot phishing emails, spoofed domains, and unusual requests for urgency or confidentiality.
-
Use Email Security Tools: Deploy advanced email filtering, anti-spoofing technologies, and alerts for emails from external sources.
-
Restrict Access to Financial Data: Limit who can initiate or approve transfers and regularly audit permissions and transaction logs.
-
Keep Software and Systems Updated: Ensure all systems, especially email platforms, are up to date with the latest security patches.
FBI's IC3 Recovery Asset Team
The FBI’s IC3 Recovery Asset Team (RAT) is designed to help victims of cyber-enabled financial fraud, particularly BEC, recover funds that have been fraudulently transferred. When a complaint is filed quickly through IC3.gov (off-site), the RAT works with financial institutions and FBI field offices to identify and freeze stolen funds before they are moved beyond reach. The team's primary goal is to minimize financial losses by intervening as swiftly as possible after a fraudulent transaction occurs.
Though the FBI’s IC3 receives an astonishing 2,000+ complaints every day, the RAT has proved to be helpful in aiding in the ultimate recovery of funds for many organizations and consumers. One such success story from Denver, Colorado was shared:
The Recovery Asset Team received a complaint reporting a BEC involving a real estate transaction. The individuals were in the process of purchasing property and received a spoofed email from their supposed real estate agents requesting that they wire $956,342 to a U.S. domestic bank to finalize the closing. Two days after the wire was initiated, the victims realized the instructions came from a spoofed email. Upon notification, the Recovery Asset Team immediately initiated the process to freeze the fraudulent recipient bank account. The transfer of $955,060 was stopped and the money was returned to the individuals.
Nacha’s Payments Innovation Alliance, of which UMACHA is a participant, developed a Response Action Plan – Business Email Compromise resource which helps address:
-
What to do if your company is a victim, including where to report the crime.
-
Preventing BEC scams.
UMACHA also offers a BEC toolkit intended to help financial institutions educate their clients and the public on how to prevent BEC. The toolkit includes a sample email template, a media release, and social media posts. UMACHA members can access the toolkit within our Free Sample Documents (Communications).
Other Trends
In 2024, the top three cybercrimes by number of victim complaints were phishing/spoofing, extortion, and personal data breaches. Investment fraud, particularly involving cryptocurrency, resulted in the highest financial losses, exceeding $6.5 billion.
The highest number of complaints came from California, Texas, and Florida. Individuals over age 60 submitted the most complaints and experienced the greatest losses, totaling nearly $5 billion.
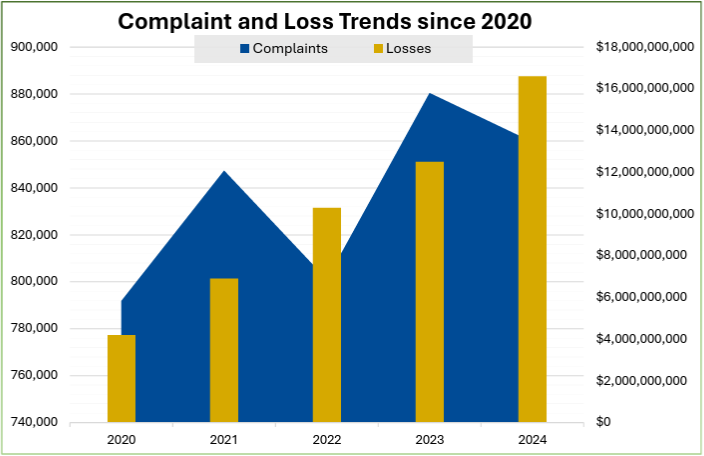
(Illustration showing the number of complaints received through IC3 and the corresponding monetary losses for calendar years 2020-2024.)
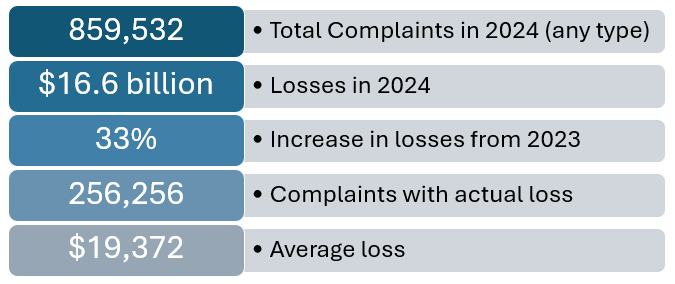
2024 by the Numbers (Infographic)
(Illustration highlighting key statistics from the 2024 Internet Crime Report.)
As cybercriminals become more sophisticated by using deepfakes, AI-generated communications, and social engineering tactics, businesses and financial institutions must adapt quickly.
Strengthening email security protocols, implementing multi-factor authentication, training employees to recognize red flags, and establishing rapid response procedures for suspicious activity are no longer optional, they’re essential. By staying informed and proactive, organizations can better defend against BEC and other cybercrimes and mitigate the financial and reputational damage that often follows.
UMACHA is Here to Help
At UMACHA, we strive to be your key partner in navigating the ever-evolving world of electronic payments. Whether you're looking to strengthen your knowledge, ensure compliance, or protect your organization from fraud, we're here to walk alongside you every step of the way.
We are offering several full-day fraud-focused events designed to equip you with the insights, tools, and strategies needed to stay ahead of emerging threats. Consider joining us for the following events:
-
Fraud Symposium (In-Person in Brooklyn Park, MN) – May 15, 2025
-
Fraud Symposium (Virtual) – May 22, 2025
-
Elder Financial Exploitation Symposium (Virtual) – June 17, 2025
-
Navigating Payments (In-Person in Brooklyn Center, MN) – September 16-17, 2025
-
Fraud Symposium (In-Person in Johnston, IA) – October 30, 2025
Stay connected with Eric Wester and UMACHA on LinkedIn!